
Security requires a comprehensive approach to be successful, and replicated helps security-conscious vendors and enterprises meet their goals. We can think of 1/ security strategy for the enterprise who wants control of their data and the apps they use, 2/ security approaches used by the vendor building the app, and 3/ security by design that’s embedded within replicated to facilitate both. This blog will explore the many layers of security that are necessary to protect apps and data in customer-controlled environments – everything, everywhere, all at once.
Some of the most common security reasons vendors and their enterprise customers like replicated include:
- Enabling enterprise private instances of apps
At our most basic level, a key value prop of replicated is how our platform enables commercial software vendors to distribute a private, enterprise-ready instance of their application into their customers’ self-managed environments. By doing so, software vendors can give their customers full control of all the data that the application processes. Additionally, by controlling the environment, end-customers can monitor and block inbound and outbound traffic to improve compliance with data controls. This helps reduce the attack surface area and number of places where sensitive data is held. Bring all the apps to the data in one secure place, rather than distribute the data to many different SaaS apps each with their own strengths and vulnerabilities!
- Performing automatic, online updates and patches
One of the most frustrating scenarios for a vendor is when their customers have data exposed through vulnerabilities that already have patches available in the latest releases of their apps. If only the customers would apply the updates in a timely way! With automatic updates, this problem can be addressed and same day patching of all instances for all customers becomes much more achievable. If the customer is running the distributed software with “online updates” then, only specific metadata (the license ID & version information) according to criteria controlled by the customer is sent to replicated to check if updates are available. At the very least, having reporting into which customers are still running vulnerable versions enables the vendors to send urgent reminders to patch.
- Air gap protection for apps and data
For the highest security, some organizations choose to implement an air gap approach - either with no physical external Internet connection at all, or more commonly an intermediate zone with virtual and/or operational air gaps. The idea is to completely isolate the apps and data from attackers, external or internal. If the customer is running the distributed software in “air gap mode” then no data leaves the system (or is even attempted) without direct action from the customer. Of course, this greatly complicates the ability to distribute an application, update it, or extract support log information. replicated provides mechanisms to facilitate deployment into air gapped environments, and all data can be redacted before sharing.
Layered Security for replicated, our Vendors, and their Customers
These three pieces above don’t tell the whole story. Let’s now look at a more complete layered security model for distributing commercial software into customer environments. Here’s a diagram showing many of the components and roughly where they can be implemented. Some security controls should of course be implemented in all three locations: in the vendor’s dev environment and app, in the customer-controlled environment, and within replicated’s own environment and platform offerings.
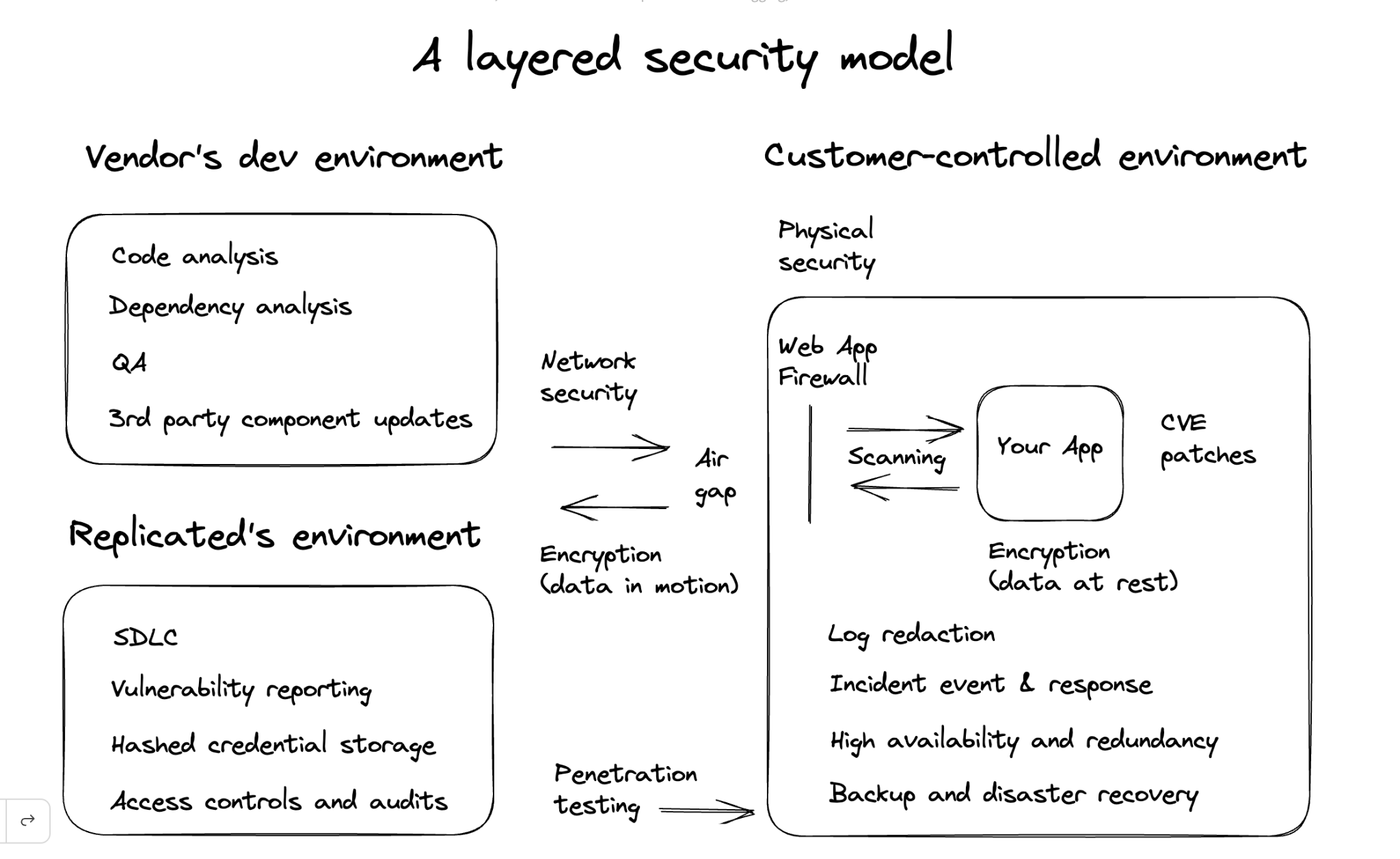
Physical Security Approaches
Facilities and location - Both vendors and enterprises should evaluate the physical security details of where they run their operations.
replicated service providers' physical infrastructure is hosted and managed within Amazon Web Services (AWS) secure data centers and utilizes AWS technology. AWS continually manages risk and undergoes recurring assessments to ensure compliance according to the industry’s standards. AWS data center operations have been accredited under:
● ISO 27001
● SOC 1 and SOC 2/SSAE 16/ISAE 3402 (Previously SAS 70 Type II)
● PCI Level 1
● FISMA Moderate
● Sarbanes-Oxley (SOX)
replicated’s service providers’ data centers are all located in the United States, but of course data sovereignty, latency or other considerations could suggest other locations for vendors and enterprises.
On-site Security - For proper on-site security, physical access is strictly controlled both at the perimeter and at building ingress points by professional security staff utilizing video surveillance, intrusion detection systems, and other electronic means. Authorized staff must pass two-factor authentication no fewer than three times to access data center floors. All visitors and contractors are required to present identification and are signed in and continually escorted by authorized staff.
replicated utilizes ISO 27001 and FISMA certified data centers managed by AWS. AWS data centers are housed in nondescript facilities, and critical facilities have extensive setback and military-grade perimeter control berms, as well as other natural boundary protection.
Network Security Approaches
Firewall and Web Application Firewall Protection - Access to sensitive systems should only be granted by a ZeroTrust implementation that analyzes the connection and the connecting device, with decisions made based on the characteristics of the request. Firewalls are utilized to restrict access to systems from external networks and between systems internally. By default, all access is denied and only explicitly allowed ports and protocols are allowed based on business need. Each system is assigned to a firewall security group based on the system’s function. Security groups restrict access to the ports and protocols required for a system’s specific function in order to mitigate risk. Host-based firewalls also provide the ability to further limit inbound and outbound connections as needed.
All firewall infrastructure (hardware and software) and management for replicated is provided by our service providers: AWS and Cloudflare. replicated also leverages a suite of Cloudflare web application firewall products to provide virtual web application firewall (WAF) that automatically blocks suspicious traffic and bots, and enables rate limiting.
Vulnerability Scanning - Managed firewalls prevent IP, MAC, and ARP spoofing on the network and between virtual hosts helps to ensure spoofing is not possible. Packet sniffing is prevented by infrastructure including the hypervisor which will not deliver traffic to any interface other than that which it is addressed. Port scanning is prohibited and every reported instance is investigated by our infrastructure provider. When port scans are detected, they are stopped and access is blocked.
replicated’s service provider utilizes application isolation, operating system restrictions, and encrypted connections to further ensure risk is mitigated at multiple levels.
Penetration Testing and Vulnerability Assessments - Third-party security testing of our service providers is performed by independent and reputable security consulting firms at least annually. Findings from each assessment are reviewed with the assessors, risk ranked, assigned to the responsible team for remediation, and then reviewed again.
Security Incident Event and Response - In the event of a security incident, engineers gather extensive logs from critical host systems and analyze them to respond to the incident in the most appropriate way possible. Gathering and analyzing log information is critical for troubleshooting and investigating issues.
Our service provider allows us to analyze four main log types: system, application, API, and audit logs from user accounts. replicated can also facilitate the collection of the application version, Kubernetes cluster config, environment info, and application logs in a (optionally redacted) support bundle for vendors who need a deeper understanding of where and how their apps are being run.
DDoS Mitigation - A service provider's infrastructure should provide distributed denial-of-service (DDoS) mitigation techniques, including TCP Syn cookies and connection rate limiting, in addition to maintaining multiple backbone connections and internal bandwidth capacity that exceeds the Internet carrier supplied bandwidth.
We work closely with our providers to quickly respond to events and enable advanced DDoS mitigation controls when needed.
Logical Access - Access to the replicated production network is restricted by an explicit need-to-know basis. It utilizes least privilege, is frequently audited, and is closely controlled by our Engineering team. Employees accessing the replicated production network are required to use multiple factors of authentication.
Encryption of Data in Transit and at Rest
Encryption - Strong encryption is a basic building block of any security strategy, and should be pervasively implemented for both data in transit (in motion) and stored data (at rest.)
Communications between customers, vendors, and replicated servers are encrypted according to industry best practices (HTTPS). replicated supports encryption of sensitive customer data at rest.
Availability & Continuity
Uptime - Uptime matters for enterprise applications because it directly impacts the availability and reliability of critical business systems and can result in financial losses, decreased productivity, and damage to reputation if service is disrupted.
replicated availability has been 100% for the previous quarter and is continuously monitored. The availability reports are available at "../6389031dde063a66806042ba/63a36f9ec780c5e9957a5d71_replicated-Security-Whitepaper.pdf" data-wf-native-id-path="ced23a98-8563-380b-27e2-68ea3774aee8"> Security White Paper.
To better understand the many ways in which replicated helps vendors securely deliver software, please check out our Secure Everything use case page.